Download VMware.5V0-41.21.VCEplus.2023-03-16.30q.tqb
| Vendor: | VMware |
| Exam Code: | 5V0-41.21 |
| Exam Name: | VMware NSX-T Data Center 3-1 Security |
| Date: | Mar 16, 2023 |
| File Size: | 485 KB |
Demo Questions
Question 1
An NSX administrator has turned on logging for the distributed firewall rule. On an ESXi host, where will the logs be stored?
- /var/log/esxupdate.log
- /var/log/dfwpktlogs.log
- /var/log/hostd.log
- /var/log/vmkerntl.log
Correct answer: B
Explanation:
The NSX administrator has enabled logging for the distributed firewall rule, and the logs are stored in the /var/log/dfwpktlogs.log file on the ESXi host. This log file stores the packet logs for the distributed firewall rules, and the logs can be used for auditing and troubleshooting the distributed firewall.Reference: https://docs.vmware.com/en/VMware-NSX-T-Data-Center/2.5/nsxt_25_admin_guide/GUID-E0CC7D8A-F9E6-4A6F-A6F8-6A3D7B3DC3EF.html#GUIDE0CC7D8A- F9E6-4A6F-A6F8-6A3D7B3DC3EF The NSX administrator has enabled logging for the distributed firewall rule, and the logs are stored in the /var/log/dfwpktlogs.log file on the ESXi host. This log file stores the packet logs for the distributed firewall rules, and the logs can be used for auditing and troubleshooting the distributed firewall.
Reference:
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/2.5/nsxt_25_admin_guide/GUID-E0CC7D8A-F9E6-4A6F-A6F8-6A3D7B3DC3EF.html#GUIDE0CC7D8A- F9E6-4A6F-A6F8-6A3D7B3DC3EF
Question 2
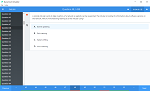
A Security Administrator needs to update their NSX Distributed IDS/IPS policy to detect new attacks with critical CVSS scoring that leads to credential theft from targeted systems.
Which actions should you take?
- Update Distributed IDS/IPS signature databaseEdit your profile from Security > Distributed IDS > ProfilesSelect Critical severity, filter on attack type and select Successful Credential Theft DetectedCheck the profile is applied in Distributed IDS rules
- Edit your Distributed IDS rule from Security > Distributed IDS/IPS > RulesFilter on attack type and select Successful Credential Theft DetectedUpdate Mode to detect and preventClick on gear icon and change direction to OUT
- Create a new profile from Security > Distributed IDS > ProfilesSelect Critical severity, filter on attack type and select Successful Credential Theft DetectedCheck the profile is applied In Distributed IDS rulesMonitor Distributed IDS alerts to validate changes are applied
- Edit your Distributed IDS rule from Security > Distributed IDS/IPS > RulesFilter on attack type and select Successful Credential Theft DetectedUpdate Mode to detect and preventClick on gear icon and change direction to IN-OUT
Correct answer: A
Explanation:
Reference:https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/nsxt_31_ids_ips/GUID-B2D6A7F6- Reference:
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/nsxt_31_ids_ips/GUID-B2D6A7F6-
Question 3
Which is an insertion point for East-West service insertion?
- tier-1 gateway
- Partner SVM
- Guest VM vNlC
- transport node
Correct answer: C
Explanation:
Reference:East-West service insertion refers to the ability to insert security services, such as firewall and intrusion detection and prevention, between virtual machines (VMs) that are communicating within the same logical network.One of the insertion points for East-West service insertion is the virtual network interface card (vNIC) of the guest VM. The vNIC is the virtual representation of a physical NIC on a VM, and it connects the VM to the virtual network. By inserting security services at the vNIC level, traffic between VMs can be inspected and secured before it reaches the virtual switch.VMware NSX-T Data Center documentation https://docs.vmware.com/en/VMware-NSX-T-Data-Center/index.htmlVMware NSX-T Data Center Security documentationhttps://docs.vmware.com/en/VMware-NSX-TData-Center/3.1/com.vmware.nsxt.security.doc/GUID-8F7C8B70-F1A6-4F31-8D6CA0A9B9C9A9D3.html Reference:
East-West service insertion refers to the ability to insert security services, such as firewall and intrusion detection and prevention, between virtual machines (VMs) that are communicating within the same logical network.
One of the insertion points for East-West service insertion is the virtual network interface card (vNIC) of the guest VM. The vNIC is the virtual representation of a physical NIC on a VM, and it connects the VM to the virtual network. By inserting security services at the vNIC level, traffic between VMs can be inspected and secured before it reaches the virtual switch.
VMware NSX-T Data Center documentation https://docs.vmware.com/en/VMware-NSX-T-Data-Center/index.html
VMware NSX-T Data Center Security documentation
https://docs.vmware.com/en/VMware-NSX-TData-Center/3.1/com.vmware.nsxt.security.doc/GUID-8F7C8B70-F1A6-4F31-8D6CA0A9B9C9A9D3.html