Download Microsoft.70-413.CertKiller.2018-06-24.30q.tqb
| Vendor: | Microsoft |
| Exam Code: | 70-413 |
| Exam Name: | Designing and Implementing a Server Infrastructure |
| Date: | Jun 24, 2018 |
| File Size: | 2 MB |
Demo Questions
Question 1
Your network contains an Active Directory domain named contoso.com. The domain contains multiple sites.
You plan to deploy DirectAccess.
The network security policy states that when client computers connect to the corporate network from the Internet, all of the traffic destined for the Internet must be routed through the corporate network.
You need to recommend a solution for the planned DirectAccess deployment that meets the security policy requirement
Solution: You set the ISATAP State to state disabled.
Does this meet the goal?
- Yes
- No
Correct answer: B
Explanation:
With NAT64 and DNS64, the DirectAccess server now has the ability to take those client IPv6 packets and spin them down into IPv4 packets, so you can simply leave your internal network all IPv4. So back in the beginning it was standard practice to enable ISATAP globally. Today, because of the known issues, it is recommended not to use ISATAP at all, unless you have a specific reason for needing itNote: ISATAP defines a method for generating a link-local IPv6 address from an IPv4 address, and a mechanism to perform Neighbor Discovery on top of IPv4. With NAT64 and DNS64, the DirectAccess server now has the ability to take those client IPv6 packets and spin them down into IPv4 packets, so you can simply leave your internal network all IPv4. So back in the beginning it was standard practice to enable ISATAP globally. Today, because of the known issues, it is recommended not to use ISATAP at all, unless you have a specific reason for needing it
Note: ISATAP defines a method for generating a link-local IPv6 address from an IPv4 address, and a mechanism to perform Neighbor Discovery on top of IPv4.
Question 2
Your network contains an Active Directory domain named contoso.com. The domain contains multiple sites.
You plan to deploy DirectAccess.
The network security policy states that when client computers connect to the corporate network from the Internet, all of the traffic destined for the Internet must be routed through the corporate network.
You need to recommend a solution for the planned DirectAccess deployment that meets the security policy requirement.
Solution: You enable split tunneling.
Does this meet the goal?
- Yes
- No
Correct answer: B
Explanation:
DirectAccess by default enables split tunneling. All traffic destined to the corpnet is sent over the DA IPsec tunnels, and all traffic destined for the Internet is sent directly to the Internet over the local interface. This prevents DA clients from bringing the corporate Internet connection to its knees.Is DA split tunneling really a problem? The answer is no.Why? Because the risks that exist with VPNs, where the machine can act as a router between the Internet and the corporate network is not valid with DirectAccess. IPsec rules on the UAG server require that traffic be from an authenticated source, and all traffic between the DA client and server is protected with IPsec.Thus, in the scenario where the DA client might be configured as a router, the source of the traffic isn’t going to be the DA client, and authentication will fail – hence preventing the type of routing that VPN admins are concerned about. DirectAccess by default enables split tunneling. All traffic destined to the corpnet is sent over the DA IPsec tunnels, and all traffic destined for the Internet is sent directly to the Internet over the local interface. This prevents DA clients from bringing the corporate Internet connection to its knees.
Is DA split tunneling really a problem? The answer is no.
Why? Because the risks that exist with VPNs, where the machine can act as a router between the Internet and the corporate network is not valid with DirectAccess. IPsec rules on the UAG server require that traffic be from an authenticated source, and all traffic between the DA client and server is protected with IPsec.
Thus, in the scenario where the DA client might be configured as a router, the source of the traffic isn’t going to be the DA client, and authentication will fail – hence preventing the type of routing that VPN admins are concerned about.
Question 3
Your network contains an Active Directory domain named contoso.com. The domain contains three VLANs. The VLANs are configured as shown in the following table.
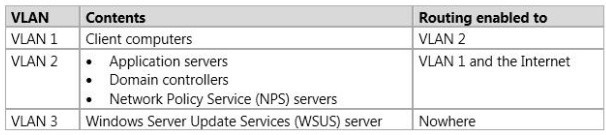
All client computers run either Windows 7 or Windows 8.
Goal: You need to implement a solution to ensure that only the client computers that have all of the required security updates installed can connect to VLAN 1. The solution must ensure that all other client computers connect to VLAN 3.
Solution: You implement the 802.1x Network Access Protection (NAP) enforcement method.
Does this meet the goal?
- Yes
- No
Correct answer: A
Explanation:
NAP supports a variety of what we call enforcement methods. In the NAP space, and enforcement method is simply a term that defines the way a machine connects to a network. In NAP, these are DHCP, 802.1x (wired or wireless), VPN, IPsec, or via a Terminal Services Gateway. NAP supports a variety of what we call enforcement methods. In the NAP space, and enforcement method is simply a term that defines the way a machine connects to a network. In NAP, these are DHCP, 802.1x (wired or wireless), VPN, IPsec, or via a Terminal Services Gateway.