Download IBM.C1000-162.VCEDumps.2024-03-26.38q.tqb
| Vendor: | IBM |
| Exam Code: | C1000-162 |
| Exam Name: | IBM Certified Analyst - Security QRadar SIEM V7.5 |
| Date: | Mar 26, 2024 |
| File Size: | 319 KB |
Demo Questions
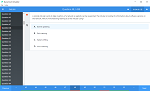
Question 1
Which of these statements regarding the deletion of a generated content report is true?
- Only specific reports that were not generated from the report template as well as the report template are deleted.
- All reports that were generated from the report template are deleted, but the report template is retained.
- All reports that were generated from the report template as well as the report template are deleted.
- Only specific reports that were not generated from the report template are deleted, but the report template is retained.
Correct answer: B
Explanation:
When deleting a generated content report in QRadar, all reports that were generated from the report template are deleted, but the report template itself is retained. This ensures that the structure for generating future reports remains intact, while only the instances of reports generated from that template are removed. When deleting a generated content report in QRadar, all reports that were generated from the report template are deleted, but the report template itself is retained. This ensures that the structure for generating future reports remains intact, while only the instances of reports generated from that template are removed.
Question 2
When examining lime fields on Event Information, which one represents the time QRadar received the raw event?
- Processing Time
- Log Source Time
- Start Time
- Storage Time
Correct answer: C
Explanation:
The 'Start Time' timestamp represents when an event is received by a QRadar Event Collector, marking the moment QRadar first becomes aware of the event. This is crucial for understanding the timing of event processing and potential delays in the event pipeline. The 'Start Time' timestamp represents when an event is received by a QRadar Event Collector, marking the moment QRadar first becomes aware of the event. This is crucial for understanding the timing of event processing and potential delays in the event pipeline.
Question 3
A Security Analyst was asked to search for an offense on a specific day. The requester was not sore of the time frame, but had Source Host information to use as well as networks involved, Destination IP and username.
Which fitters can the Security Analyst use to search for the information requested?
- Offense ID, Source IP, Username
- Magnitude, Source IP, Destination IP
- Description, Destination IP. Host Name
- Specific Interval, Username, Destination IP
Correct answer: D