Download Fortinet.NSE7_ZTA-7.2.VCEplus.2024-02-15.18q.tqb
| Vendor: | Fortinet |
| Exam Code: | NSE7_ZTA-7.2 |
| Exam Name: | Fortinet NSE 7 - Zero Trust Access 7-2 |
| Date: | Feb 15, 2024 |
| File Size: | 2 MB |
Demo Questions
Question 1
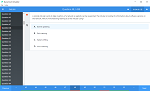
Which three methods can you use to trigger layer 2 polling on FortiNAC? (Choose three)
- Polling scripts
- Link traps
- Manual polling
- Scheduled tasks
- Polling using API
Correct answer: ACD
Explanation:
To trigger layer 2 polling on FortiNAC, the three methods are:A) Polling scripts: These are scripts configured within FortiNAC to actively poll the network at layer 2 to gather information about connected devices.C) Manual polling: This involves manually initiating a polling process from the FortiNAC interface to gather current network information.D) Scheduled tasks: Polling can be scheduled as regular tasks within FortiNAC, allowing for automated, periodic collection of network data.The other options are not standard methods for layer 2 polling in FortiNAC:B) Link traps: These are more related to SNMP trap messages rather than layer 2 polling.E) Polling using API: While APIs are used for various integrations, they are not typically used for initiating layer 2 polling in FortiNAC.FortiNAC Layer 2 Polling Documentation.Configuring Polling Methods in FortiNAC. To trigger layer 2 polling on FortiNAC, the three methods are:
A) Polling scripts: These are scripts configured within FortiNAC to actively poll the network at layer 2 to gather information about connected devices.
C) Manual polling: This involves manually initiating a polling process from the FortiNAC interface to gather current network information.
D) Scheduled tasks: Polling can be scheduled as regular tasks within FortiNAC, allowing for automated, periodic collection of network data.
The other options are not standard methods for layer 2 polling in FortiNAC:
B) Link traps: These are more related to SNMP trap messages rather than layer 2 polling.
E) Polling using API: While APIs are used for various integrations, they are not typically used for initiating layer 2 polling in FortiNAC.
FortiNAC Layer 2 Polling Documentation.
Configuring Polling Methods in FortiNAC.
Question 2
Which two statements are true regarding certificate-based authentication for ZTNA deployment? (Choose two.)
- FortiGate signs the client certificate submitted by FortiClient.
- The default action for empty certificates is block
- Certificate actions can be configured only on the FortiGate CLI
- Client certificate configuration is a mandatory component for ZTNA
Correct answer: BD
Explanation:
Certificate-based authentication is a method of verifying the identity of a device or user by using a digital certificate issued by a trusted authority. For ZTNA deployment, certificate-based authentication is used to ensure that only authorized devices and users can access the protected applications or resources.B) The default action for empty certificates is block. This is true because ZTNA requires both device and user verification before granting access. If a device does not have a valid certificate issued by the ZTNA CA, it will be blocked by the ZTNA gateway. This prevents unauthorized or compromised devices from accessing the network.D) Client certificate configuration is a mandatory component for ZTNA. This is true because ZTNA relies on client certificates to identify and authenticate devices. Client certificates are generated by the ZTNA CA and contain the device ID, ZTNA tags, and other information. Client certificates are distributed to devices by the ZTNA management server (such as EMS) and are used to establish a secure connection with the ZTNA gateway.A) FortiGate signs the client certificate submitted by FortiClient. This is false because FortiGate does not sign the client certificates. The client certificates are signed by the ZTNA CA, which is a separate entity from FortiGate.FortiGate only verifies the client certificates and performs certificate actions based on the ZTNA tags.C) Certificate actions can be configured only on the FortiGate CLI. This is false because certificate actions can be configured on both the FortiGate GUI and CLI. Certificate actions are the actions that FortiGate takes based on the ZTNA tags in the client certificates. For example, FortiGate can allow, block, or redirect traffic based on the ZTNA tags.1: Technical Tip: ZTNA for Corporate hosts with SAML authentication and FortiAuthenticator as IDP2: Zero Trust Network Access - Fortinet Certificate-based authentication is a method of verifying the identity of a device or user by using a digital certificate issued by a trusted authority. For ZTNA deployment, certificate-based authentication is used to ensure that only authorized devices and users can access the protected applications or resources.
B) The default action for empty certificates is block. This is true because ZTNA requires both device and user verification before granting access. If a device does not have a valid certificate issued by the ZTNA CA, it will be blocked by the ZTNA gateway. This prevents unauthorized or compromised devices from accessing the network.
D) Client certificate configuration is a mandatory component for ZTNA. This is true because ZTNA relies on client certificates to identify and authenticate devices. Client certificates are generated by the ZTNA CA and contain the device ID, ZTNA tags, and other information. Client certificates are distributed to devices by the ZTNA management server (such as EMS) and are used to establish a secure connection with the ZTNA gateway.
A) FortiGate signs the client certificate submitted by FortiClient. This is false because FortiGate does not sign the client certificates. The client certificates are signed by the ZTNA CA, which is a separate entity from FortiGate.
FortiGate only verifies the client certificates and performs certificate actions based on the ZTNA tags.
C) Certificate actions can be configured only on the FortiGate CLI. This is false because certificate actions can be configured on both the FortiGate GUI and CLI. Certificate actions are the actions that FortiGate takes based on the ZTNA tags in the client certificates. For example, FortiGate can allow, block, or redirect traffic based on the ZTNA tags.
1: Technical Tip: ZTNA for Corporate hosts with SAML authentication and FortiAuthenticator as IDP
2: Zero Trust Network Access - Fortinet
Question 3
Which one of the supported communication methods does FortiNAC use for initial device identification during discovery?
- LLDP
- SNMP
- API
- SSH
Correct answer: B
Explanation:
FortiNAC uses a variety of methods to identify devices on the network, such as Vendor OUI, DHCP fingerprinting, and device profiling12.One of the supported communication methods that FortiNAC uses for initial device identification during discovery is SNMP (Simple Network Management Protocol)3.SNMP is a protocol that allows network devices to exchange information and monitor their status4.FortiNAC can use SNMP to read information from switches and routers, such as MAC addresses, IP addresses, VLANs, and port status3.SNMP can also be used to configure network devices and enforce policies4.Reference:1: Identification | FortiNAC 9.4.0 - Fortinet Documentation2: Device profiling process | FortiNAC 8.3.0 | Fortinet Document Library3: Using FortiNAC to identify medical devices - James Pratt4: How does FortiNAC identify a new device on the network? FortiNAC uses a variety of methods to identify devices on the network, such as Vendor OUI, DHCP fingerprinting, and device profiling12.One of the supported communication methods that FortiNAC uses for initial device identification during discovery is SNMP (Simple Network Management Protocol)3.SNMP is a protocol that allows network devices to exchange information and monitor their status4.FortiNAC can use SNMP to read information from switches and routers, such as MAC addresses, IP addresses, VLANs, and port status3.SNMP can also be used to configure network devices and enforce policies4.Reference:1: Identification | FortiNAC 9.4.0 - Fortinet Documentation2: Device profiling process | FortiNAC 8.3.0 | Fortinet Document Library3: Using FortiNAC to identify medical devices - James Pratt4: How does FortiNAC identify a new device on the network?